As always, hackers utilize all possible roads to get to their destination. Latest news in this Covid-19 pandemic being, oxygen supply scarcity and staying safe, hackers have taken this route now to spread their fake oximeter apps and lure the victims into installing an Android Banking Trojan.
These fake oximeter apps target Indian users, let us see how one such app works.
Analysing one of the fake oximeter apps, “Oximeter O2” revealed that, this app
- Masquerades as blood oxygen saturation level checker app
- Spreads via SMS and WhatsApp spamming out malicious links to the members in the contact list, hxxps[://mega[.nz/file/Zhh0RSJQ#81GUF7ruoEv9itdyh_kswLlBYWoAe0TwMLt4MTM9V4g
- Specifically targets Indian users, as it prepends “+91” with the numbers in the contact list to verify if the contact has WhatsApp installed
- Downloads the sample “Oxygen Saturation Checker.apk” from the above link which is the Anubis Banking Trojan for Android
Once installed the “Oximeter O2” app looks as shown in Figures 1 & 2.

When launched, it brings up the WhatsApp media forward screen and informs the victim that the contact (from victim’s contact list) is not on WhatsApp and to add the contact as shown in Figure 3.
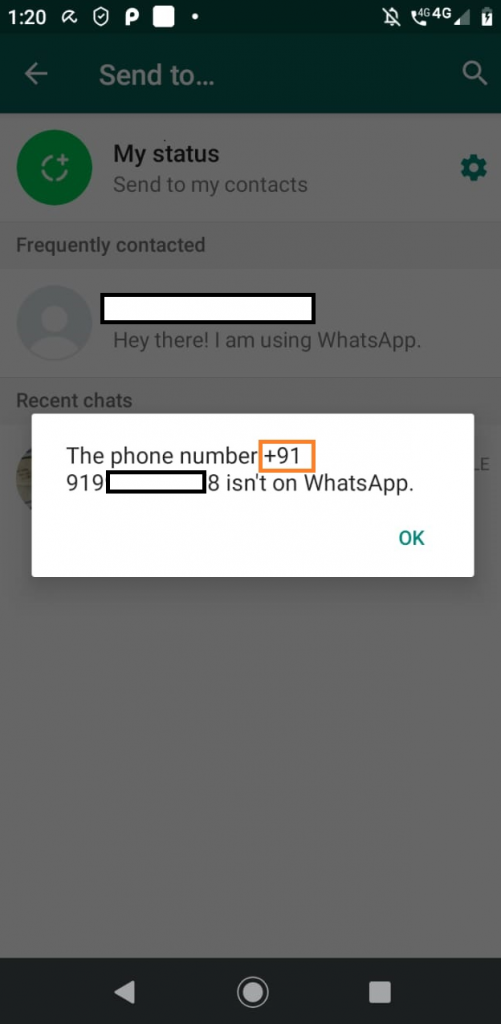
It is to be noted from Figure 3 that it is prepending “+91” to the numbers in the contact list to confirm if the contact is on WhatsApp or not, indicating that this fake app targets the Indian users.
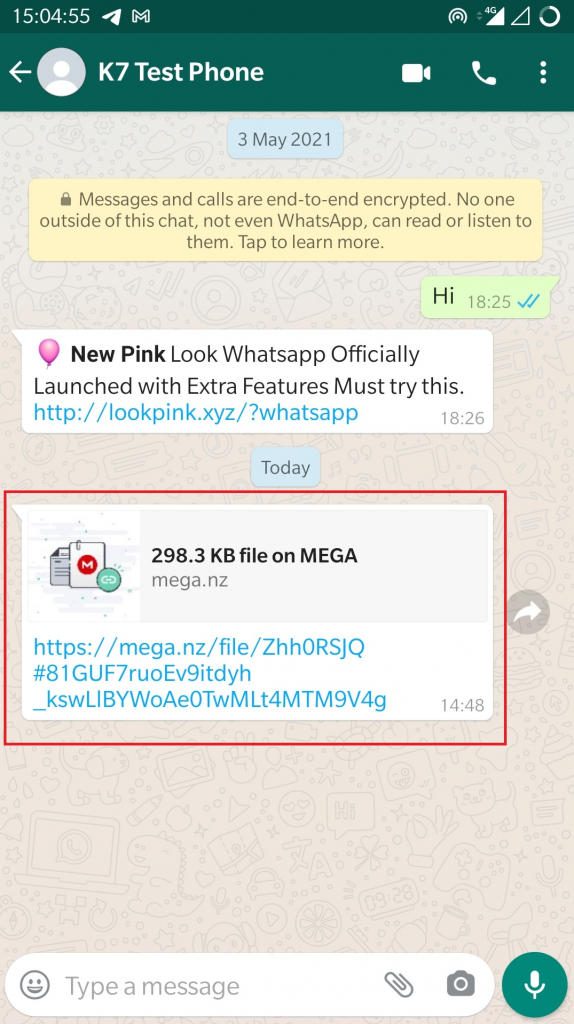
However, if the contact is added to WhatsApp or already present on WhatsApp, it forwards the same download link as shown in Figure 4.
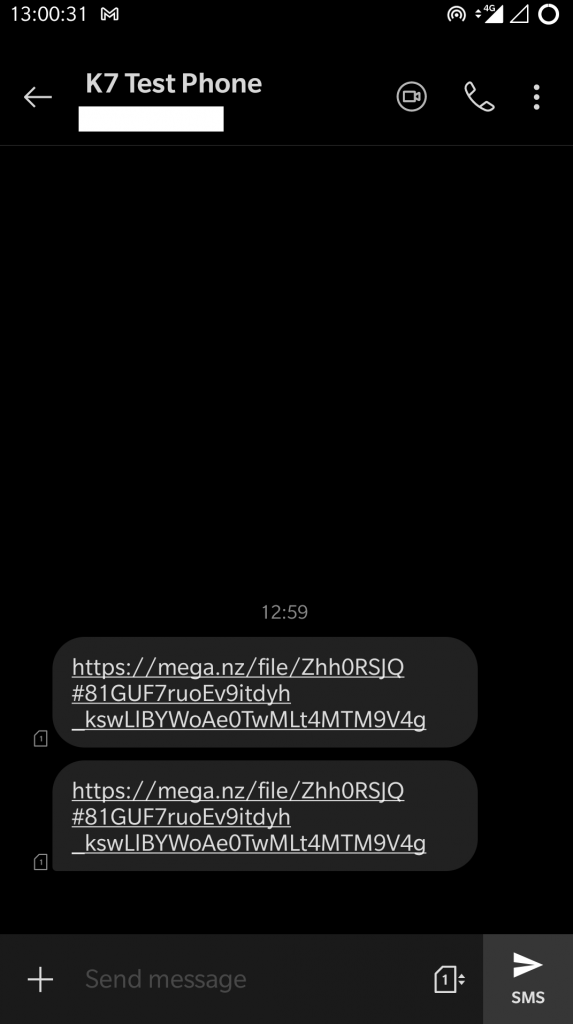
If the contact is not on WhatsApp, it forwards an SMS with the malicious link to download the same app as shown in Figure 5.
Downloaded Banking Trojan
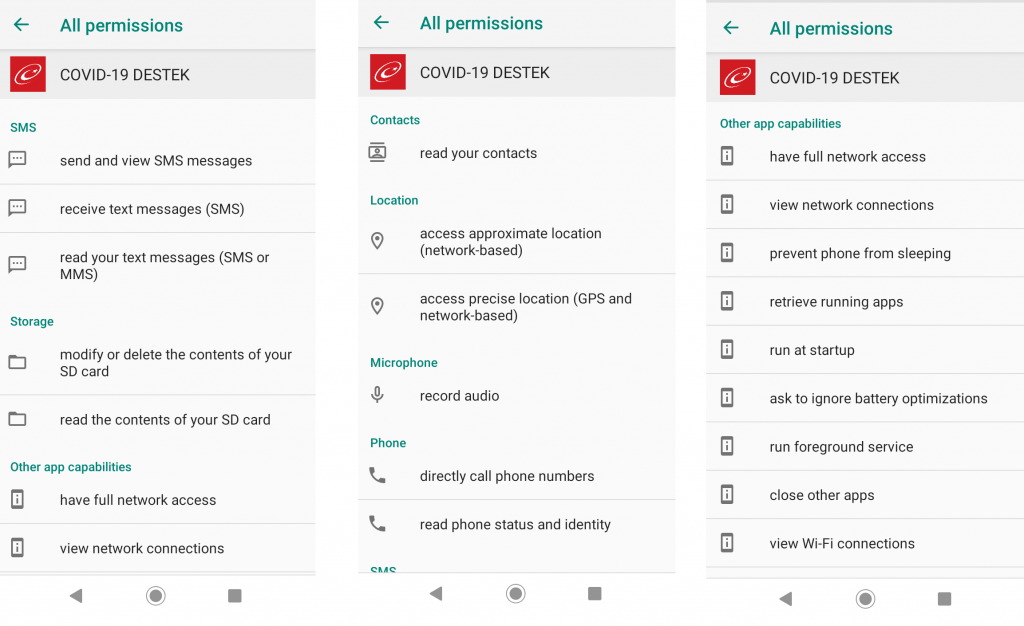
When the downloaded sample “Oxygen Saturation Checker.apk” is executed, it installs as “COVID-19 DESTEK” as shown in Figure 6

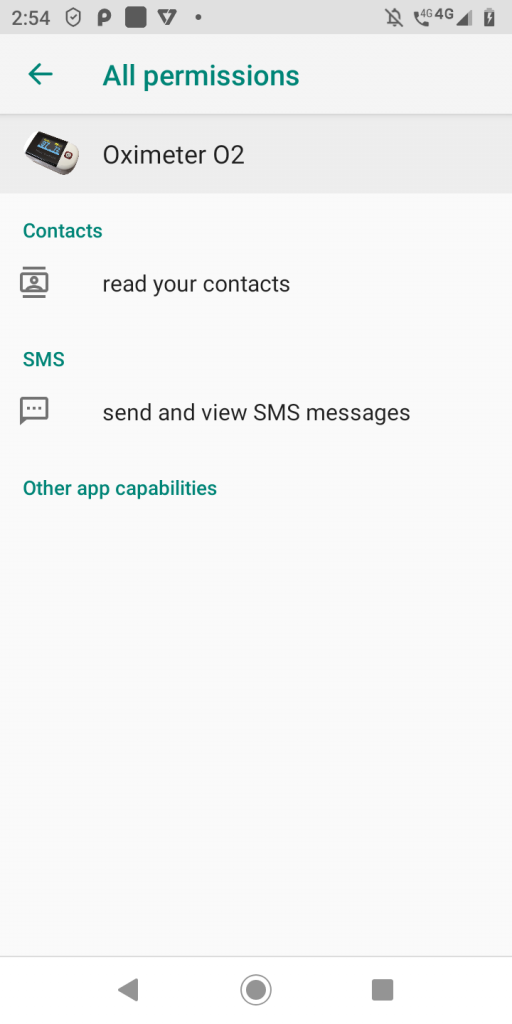
and it asks for a set of permissions to
- send and view SMS
- make calls
- fetch location information
- read contacts
- access external storage
and other capabilities as listed below to
- record audio
- full network access
- retrieve and kill running apps
- close other apps
- run at startup
As any other Banking Trojan, this malware steals banking credentials, OTP SMSes and forwards these to the hacker. For further reading on Banking Trojans, please refer to our previous blog post.
Recently, we are witnessing an increased number of attacks via SMS or WhatsApp messages with links targeting Indian users. We strongly recommend users not to click these links and also not download apps from any other source or URLs apart from the official Google Play Store. Also our readers are recommended to install a reputed security software like K7 Mobile Security to stay safe against such attacks.
Indicators Of Compromise (IOCs)
Downloader samples
| App Name | Package Name | MD5 | K7 Detection Name |
| Oximeter O2 | com.body.saturation.oximetero2 | 84684e063b664aa2d1b8c5441d1fb1b9 | Trojan ( 0001140e1 ) |
| Oximeter-H | com.vphealthy.oximeter | 408373dab2fc8d72f58a0b2aa468a1c8 | Trojan ( 0053576b1 ) |
| OXI tracker | com.blt.oximeter | acd1ef25823bbfee1162489c54df4c46 | Adware ( 0052d5ec1 ) |
Downloaded file
| App Name | Package Name | MD5 | K7 Detection Name |
| COVID-19 DESTEK | jnised.vpudbr.ifxvyx | 7f62b553f3d9a9e28d7831d83eb06663 | Trojan ( 005768471 ) |