O Estado de Ransomware no Governo 2021
Ransomware has fast become a national emergency with government organizations regularly falling victim to attack. Discover the realities behind the headlines with the new Sophos report The State of Ransomware in Government 2021.
Based on an independent survey of 117 IT managers in central government and non-departmental public bodies (NDPB), and 131 IT managers in local government organizations around the globe, it provides fresh insights into the realities of ransomware from the front line.
The report explores how ransomware impacts government organizations, and their ability to defend against these attacks. It also reveals that local government and central government have very different experiences of ransomware, and different challenges to address.
Local government – trapped in a vicious cycle
The survey revealed that local government is trapped in a vicious ransomware cycle from which is appears unable to escape.
Local government is the sector least able to stop the attackers from encrypting their data. 69% of local government organizations that were hit by ransomware had their data encrypted, compared with a cross-sector average of 54%.
Once the data is encrypted, local government is also the sector least able to restore data using backups, with only 42% of getting their data back in this way.
Perhaps as a result of this inability to use backups, local government has the second highest propensity to pay the ransom, with 42% of organizations whose data was encrypted choosing to pay up to get their data back. Only the infrastructure sector (43%) had a higher rate of payment.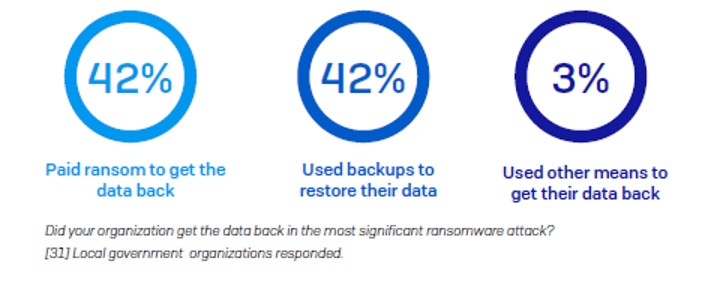
Recovering from ransomware costs local government organizations on average US$1.64 million per attack when you add together downtime, people time, device cost, network cost, lost opportunity, ransom paid, and so on. This is a little below the cross-sector average of US$1.85 million, likely because local government organizations often have smaller budgets, limiting the amount of money available to be spent on remediation.
Central government – facing a new attack approach
Central government is better able to defend against ransomware than local government, but now faces extortion-style attacks.
While central government and NDPB experienced an above-average level of attacks last year (40% vs. average of 37%), they were able to stop just over half (51%) of them before the data was encrypted. They also are better able than many other sectors to restore data using backups (61% vs. average of 57%).
Likely influenced by their ability to use backups, central government is one of the sectors least likely to pay the ransom to get their data back, with just 26% admitting to submitting to the attackers’ demands.
However, in the face of – and perhaps due to – this success, adversaries are changing their tactics. Central government organizations are almost twice as likely as the global average to experience extortion-style attacks where adversaries don’t encrypt data but hold them to ransom anyway by threatening to publish their data.
Overall, central government reports ransomware remediation costs of US$1.37 million per attack. This is much lower than the global average (US$1.85 million), likely reflecting this sector’s strong ability to use backups to restore data and its lower dependence on making ransom payments.
Paying up doesn’t pay off
What attackers omit to say when issuing ransom demands is that even if you pay, your chances of getting all your data back are slim. On average, organizations that paid the ransom got back just 65% of their data, leaving over one third of their data inaccessible.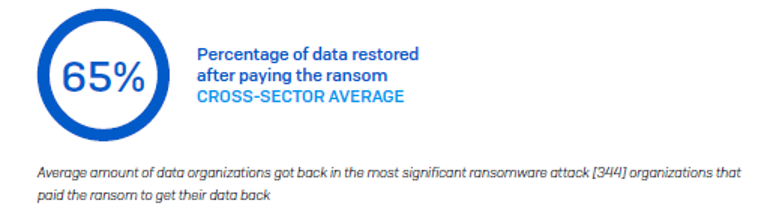
The number of respondents to this question from the government sector is too low to be statistically robust. However, anecdotally, central government got back on average 63% of their data after paying the ransom. Local government fared a little better, getting back on average 70% of but still leaving a considerable proportion of data inaccessible.
Across all sectors, 29% of organizations got back 50% or less of their data, and only 8% got all their data back.
Read the full report
Read the full State of Ransomware in Government 2021 report to learn more about the experiences and challenges facing the local and central government sectors.
The report also includes six recommendations that all organizations should follow to minimize their risk of being hit by ransomware in the future.
Pesquisa
Fabricantes
- Stormshield
- Code42
- Stormshield
- Titan HQ
- Ubiquiti
- MailStore
- Hitachi
- Solarwinds
- MailStore
- Stormshield
- Solarwinds
- Kemp
- MailStore
- ActivTrack
- Wasabi
- Avtech
- Sophos
- Wasabi
- Sem categoria
- Avtech
- Retrospect
- Aternity
- Nakivo
- Retrospect
- Peplink
- AVTECH
- Nakivo
- Riverbed
- Creative
- Solarwinds
- Aternity
- Soliton
- General
- Hitachi
- ActivTrack
- Ubiquiti
- Insights
- K7 Security
- K7 Computing
- Sophos
- Tech
- Titan HQ
- Kemp
- K7 Computing
- World
- Wasabi
- Riverbed
- Code42
- Uncategorized
- ActivTrak
- ownCloud
- Code42
- Sofia Testes
- Sophos
- Retrospect
- OwnCloud
- Aternity
- Soliton
- NAKIVO
- OwnCloud
- Titan HQ
Etiquetas
Categorias
- ownCloud
- Code42
- Sofia Testes
- Sem categoria
- Retrospect
- OwnCloud
- Aternity
- K7 Security
- NAKIVO
- OwnCloud
- Titan HQ
- Titan HQ
- Code42
- Stormshield
- Titan HQ
- Wasabi
- MailStore
- Hitachi
- Solarwinds
- ActivTrak
- MailStore
- Stormshield
- Solarwinds
- Sophos
- MailStore
- ActivTrack
- Wasabi
- Soliton
- Avtech
- Sophos
- Wasabi
- Stormshield
- Avtech
- Retrospect
- Peplink
- Ubiquiti
- Nakivo
- Retrospect
- Creative
- Kemp
- Nakivo
- Riverbed
- General
- Aternity
- Aternity
- Soliton
- Insights
- AVTECH
- ActivTrack
- Ubiquiti
- Tech
- Solarwinds
- K7 Computing
- Sophos
- World
- Hitachi
- Kemp
- K7 Computing
- Riverbed
- Code42
- Uncategorized
